Getting Started (New! for Pi 4 and also Pi 3B+)
Prepare
- Raspberry Pi 4 (or Pi 3B+) with SD card (>=8GB), 2 pcs.
- ALFA Netowrk's 802.11ah PiHAT module -- AHPI7292S, 2 pcs.
- Antennas for 802.11ah frequencies, 2 pcs.
Network Topology
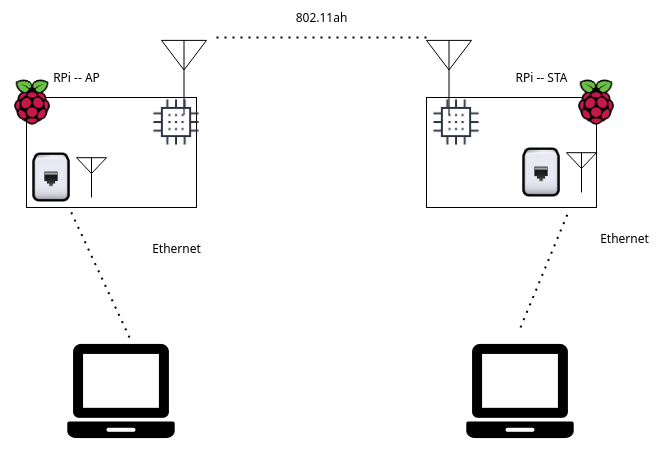
Note
We provide the software based on Newracom's EVK, which turns off the Raspberry Pi's internal WiFi and Bluetooth.
Installation
Step 1. Flash SD cards for RPi
First, please flash two SD cards with official Raspberry Pi OS (32-bit) image, one is for client and another is for AP.
Note
The image we tested is the Raspberry Pi OS (32-bit), released date: 2022-04-04.
Note
If you don't want to go through the whole setup process, you can choose to download our prebuilt image: >> DOWNLOAD <<. The prebuilt image won't update periodically. If you want to test latest software, we strongly recommend you to go throughtout the one-liner setup in following sections.
For common users, we recommend using Raspberry Pi's official tool, Raspberry Pi Imager, to flash the SD cards.
You can download the software here:
and follow its step-by-step tutorial youtube video to flash SD cards:
How to use Raspberry Pi Imager
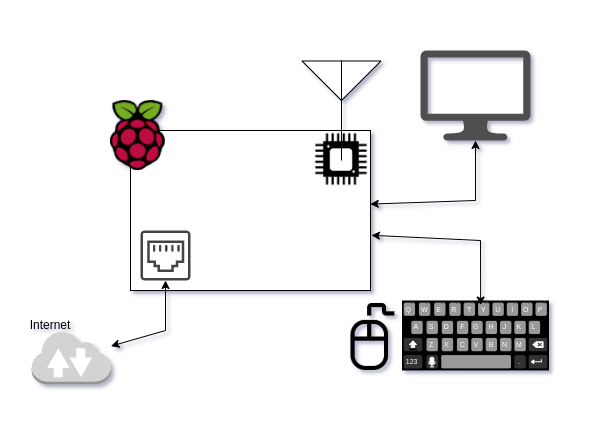
Step 2. Install SD cards to RPi, connect the cables, and power on the devices

Insert the SD card to Raspberry Pi's slot, and then power on the board by micro-USB power plug.
The setup process requires internet access, we recommend connect the devices as below during the installation process:
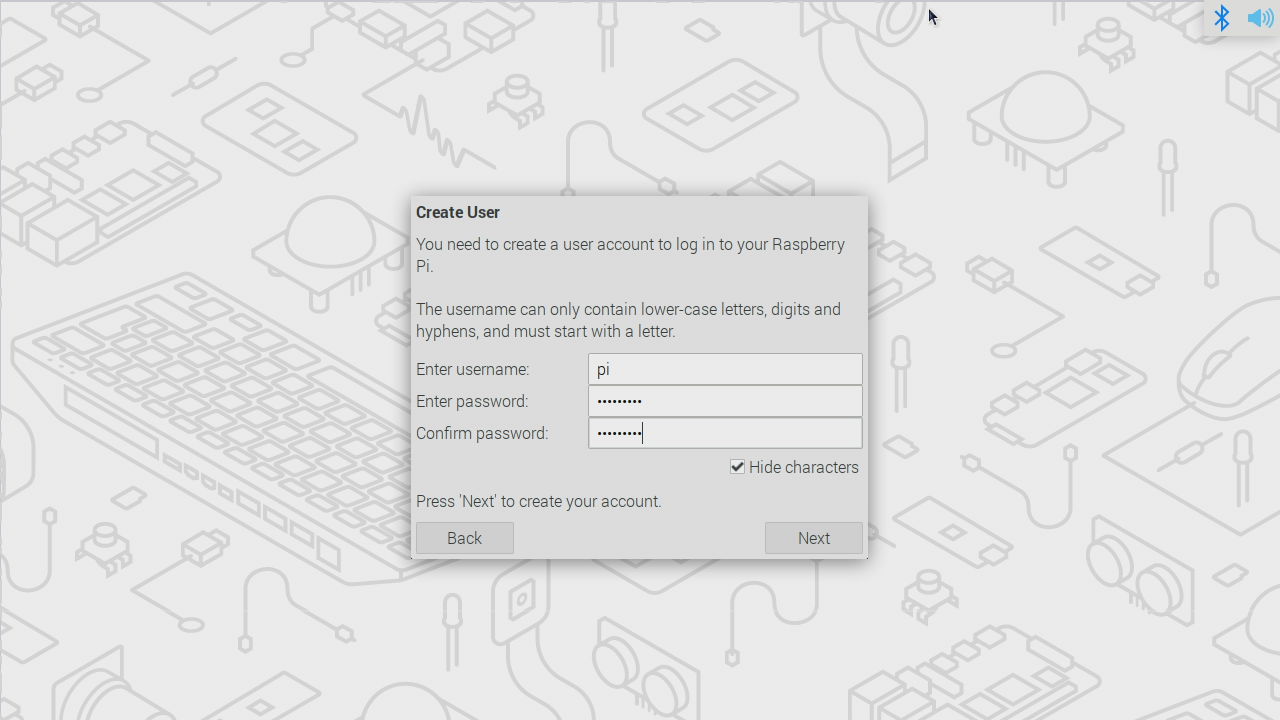
Step 3. Setup the initial desktop environment and open the terminal
For new versions since 2022-04-04, the default username needs to be specified by the user.
To make the NRC7292 EVK work, it's required to use pi as the default username here.
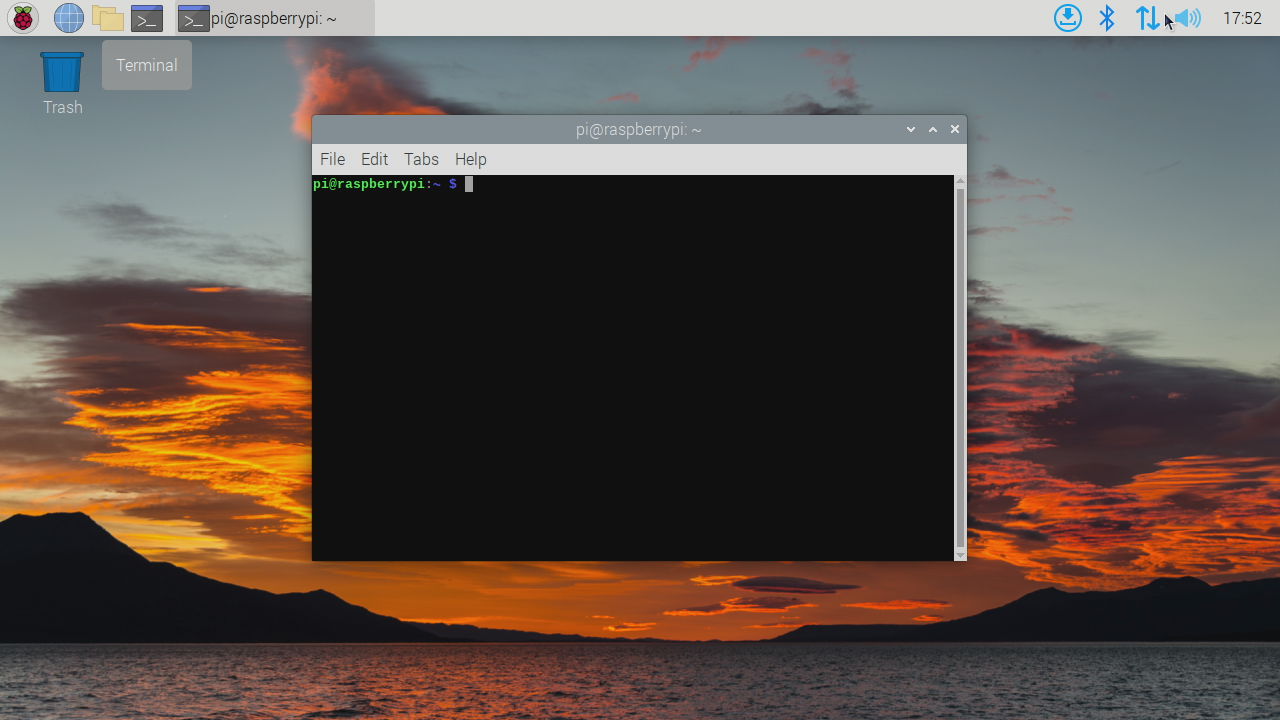
When the initial setup complete and reboot, the desktop apears and you can click the terminal icon on the panel, and get the terminal as below:
Step 4. Setup the software with an one-liner command
Execute the one-liner command to run setup script automatically:
curl -sL https://downloads.alfa.com.tw/raspbian/nrc7292_setup.sh.txt | bash -
Since the setup script will install kernel related packages and tweak system-level settings, it requies 1~2 times reboot. If you see the following dialog message, please press any key to continue the process.
When it shows the end messages (as below), the setup process are done.
[Done] The setup program finished.
Step 5. Start the program
For AP side
~/nrc_pkg/script/start.py 1 0 US
For Client side
~/nrc_pkg/script/start.py 0 0 US
Appendix
Usage of start.py
The startup program's, start.py, usage is below:
Usage:
start.py [sta_type] [security_mode] [country] [channel] [sniffer_mode]
start.py [sta_type] [security_mode] [country] [mesh_mode] [mesh_peering] [mesh_ip]
Argument:
sta_type [0:STA | 1:AP | 2:SNIFFER | 3:RELAY | 4:MESH]
security_mode [0:Open | 1:WPA2-PSK | 2:WPA3-OWE | 3:WPA3-SAE | 4:WPS-PBC]
country [US:USA | JP:Japan | TW:Taiwan | EU:EURO | CN:China |
AU:Australia | NZ:New Zealand]
-----------------------------------------------------------
channel [S1G Channel Number] * Only for Sniffer
sniffer_mode [0:Local | 1:Remote] * Only for Sniffer
mesh_mode [0:MPP | 1:MP | 2:MAP] * Only for Mesh
mesh_peering [Peer MAC address] * Only for Mesh
mesh_ip [Static IP address] * Only for Mesh
Example:
OPEN mode STA for US : ./start.py 0 0 US
Security mode AP for US : ./start.py 1 1 US
Local Sniffer mode on CH 40 for Japan : ./start.py 2 0 JP 40 0
SAE mode Mesh AP for US : ./start.py 4 3 US 2
Mesh Point with static ip : ./start.py 4 3 US 1 192.168.222.1
Mesh Point with manual peering : ./start.py 4 3 US 1 8c:0f:fa:00:29:46
Mesh Point with manual peering & ip : ./start.py 4 3 US 1 8c:0f:fa:00:29:46 192.168.222.1
Note:
sniffer_mode should be set as '1' when running sniffer on remote terminal
MPP, MP mode support only Open, WPA3-SAE security mode